How To Enable Pop up window in Safari
Some sites or web Applications need the pop-up window enable.
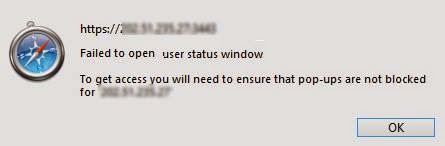
To enable pop-up windows in Safari browser :
Go to Preference menu
Choose Security tab
Uncheck Block pop-up windows

It's all that matters.
Before a company / organization benefit from cloud computing, there are
several aspects relating to Security and Privacy below that must be
considered:
1. Risk Management and Compliance - organizations are starting to adopt
the cloud still be responsible for aspects of security management, risk,
and compliance with the rules applicable in the related industry. Risk
and compliance management requires a strong internal team and the
transparency of the process of cloud service providers.
Recommendation: cloud service providers have to use some or best
practice frameworks such as MOF, or ITIL, and have certifications such
as ISO / IEC 27001:2005, and publish the audit report to the SAS 70 Type
II. In addition, according to provisions of a state, may also have to
adhere to the PCI or FISMA.
2. Access and Identity Management - Identity can be obtained through
some cloud service providers, and must be interoperable between
different organizations, different cloud providers, and based on strong
process.
Recommendation: Authentication is recommended to use several factors at
once, such as biometrics, one time password tokens (such as token BCA),
ID card with a chip, and a password.
3. Integrity of Service - cloud-based services must be built with a
foundation of strong security, and operational processes must also be
integrated with security management in the organization. The cloud
service provider must follow the process that can be proven,
well-defined, and clearly in integrating security and privacy in
services ranging from the earliest point, at any point in the cycle,
until the final. Besides security management and auditing must be
aligned between cloud providers and customers.
Recommendation: Use such certification EAL4 + (for security evaluation),
SDL (for application development), ISO / IEC 18 044 (for incident
response)
4. Integrity Client - cloud services that are used on the client side
should pay attention to aspects of security, compliance, and integrity
on the client side. Integrity client can be improved by using a
combination of best practices.
Recommendation: Strengthen the desktop system, make sure the health of
desktop systems, apply the appropriate IT policy, identity federation,
Network Access Protection and so on.
5. Information Protection - Services cloud requires a reliable process
to protect the information before, during, and after the transaction.
Take advantage of data classification to improve the control of the data
is ready to be released into the clouds.
Recommendation: Use encryption technology and information rights
management (IRM) prior to data released to the cloud.
Tips
If an interested company to implement cloud services, here are some
tips:
Start with small things first, such as utilizing cloud services as
below: Email, Calendars, Contact, Messenger, Storage, Document /
Productivity, Photo, Group, News / Sport / Wheather, Synchronization
Devices (live mesh), Family Safety, Mobile, Map
Map business requirements to a cloud service, do not do the opposite.
Not necessarily cheaper cloud services, calculate the overall cost if
the system is used in full. Compare with the local system (on premise),
and also studied the possibility of combining the cloud service with
local system
Make the process of socialization and learning about cloud services to
all employees in the company
Study the possibility of technical issues such as interoperability,
architecture, and integration. Make sure that the format of files
created through the cloud services are also exactly the same as a local
application on the client side
Copy and WIN : http://bit.ly/copynwin
Copy and WIN : http://bit.ly/copynwin
It's all that matters.
Before a company / organization benefit from cloud computing, there are
several aspects relating to Security and Privacy below that must be
considered:
1. Risk Management and Compliance - organizations are starting to adopt
the cloud still be responsible for aspects of security management, risk,
and compliance with the rules applicable in the related industry. Risk
and compliance management requires a strong internal team and the
transparency of the process of cloud service providers.
Recommendation: cloud service providers have to use some or best
practice frameworks such as MOF, or ITIL, and have certifications such
as ISO / IEC 27001:2005, and publish the audit report to the SAS 70 Type
II. In addition, according to provisions of a state, may also have to
adhere to the PCI or FISMA.
2. Access and Identity Management - Identity can be obtained through
some cloud service providers, and must be interoperable between
different organizations, different cloud providers, and based on strong
process.
Recommendation: Authentication is recommended to use several factors at
once, such as biometrics, one time password tokens (such as token BCA),
ID card with a chip, and a password.
3. Integrity of Service - cloud-based services must be built with a
foundation of strong security, and operational processes must also be
integrated with security management in the organization. The cloud
service provider must follow the process that can be proven,
well-defined, and clearly in integrating security and privacy in
services ranging from the earliest point, at any point in the cycle,
until the final. Besides security management and auditing must be
aligned between cloud providers and customers.
Recommendation: Use such certification EAL4 + (for security evaluation),
SDL (for application development), ISO / IEC 18 044 (for incident
response)
4. Integrity Client - cloud services that are used on the client side
should pay attention to aspects of security, compliance, and integrity
on the client side. Integrity client can be improved by using a
combination of best practices.
Recommendation: Strengthen the desktop system, make sure the health of
desktop systems, apply the appropriate IT policy, identity federation,
Network Access Protection and so on.
5. Information Protection - Services cloud requires a reliable process
to protect the information before, during, and after the transaction.
Take advantage of data classification to improve the control of the data
is ready to be released into the clouds.
Recommendation: Use encryption technology and information rights
management (IRM) prior to data released to the cloud.
Tips
If an interested company to implement cloud services, here are some
tips:
Start with small things first, such as utilizing cloud services as
below: Email, Calendars, Contact, Messenger, Storage, Document /
Productivity, Photo, Group, News / Sport / Wheather, Synchronization
Devices (live mesh), Family Safety, Mobile, Map
Map business requirements to a cloud service, do not do the opposite.
Not necessarily cheaper cloud services, calculate the overall cost if
the system is used in full. Compare with the local system (on premise),
and also studied the possibility of combining the cloud service with
local system
Make the process of socialization and learning about cloud services to
all employees in the company
Study the possibility of technical issues such as interoperability,
architecture, and integration. Make sure that the format of files
created through the cloud services are also exactly the same as a local
application on the client side
Copy and WIN : http://bit.ly/copynwin
Copy and WIN : http://bit.ly/copynwin
It's all that matters.
Before a company / organization benefit from cloud computing, there are
several aspects relating to Security and Privacy below that must be
considered:
1. Risk Management and Compliance - organizations are starting to adopt
the cloud still be responsible for aspects of security management, risk,
and compliance with the rules applicable in the related industry. Risk
and compliance management requires a strong internal team and the
transparency of the process of cloud service providers.
Recommendation: cloud service providers have to use some or best
practice frameworks such as MOF, or ITIL, and have certifications such
as ISO / IEC 27001:2005, and publish the audit report to the SAS 70 Type
II. In addition, according to provisions of a state, may also have to
adhere to the PCI or FISMA.
2. Access and Identity Management - Identity can be obtained through
some cloud service providers, and must be interoperable between
different organizations, different cloud providers, and based on strong
process.
Recommendation: Authentication is recommended to use several factors at
once, such as biometrics, one time password tokens (such as token BCA),
ID card with a chip, and a password.
3. Integrity of Service - cloud-based services must be built with a
foundation of strong security, and operational processes must also be
integrated with security management in the organization. The cloud
service provider must follow the process that can be proven,
well-defined, and clearly in integrating security and privacy in
services ranging from the earliest point, at any point in the cycle,
until the final. Besides security management and auditing must be
aligned between cloud providers and customers.
Recommendation: Use such certification EAL4 + (for security evaluation),
SDL (for application development), ISO / IEC 18 044 (for incident
response)
4. Integrity Client - cloud services that are used on the client side
should pay attention to aspects of security, compliance, and integrity
on the client side. Integrity client can be improved by using a
combination of best practices.
Recommendation: Strengthen the desktop system, make sure the health of
desktop systems, apply the appropriate IT policy, identity federation,
Network Access Protection and so on.
5. Information Protection - Services cloud requires a reliable process
to protect the information before, during, and after the transaction.
Take advantage of data classification to improve the control of the data
is ready to be released into the clouds.
Recommendation: Use encryption technology and information rights
management (IRM) prior to data released to the cloud.
Tips
If an interested company to implement cloud services, here are some
tips:
Start with small things first, such as utilizing cloud services as
below: Email, Calendars, Contact, Messenger, Storage, Document /
Productivity, Photo, Group, News / Sport / Wheather, Synchronization
Devices (live mesh), Family Safety, Mobile, Map
Map business requirements to a cloud service, do not do the opposite.
Not necessarily cheaper cloud services, calculate the overall cost if
the system is used in full. Compare with the local system (on premise),
and also studied the possibility of combining the cloud service with
local system
Make the process of socialization and learning about cloud services to
all employees in the company
Study the possibility of technical issues such as interoperability,
architecture, and integration. Make sure that the format of files
created through the cloud services are also exactly the same as a local
application on the client side
Copy and WIN : http://bit.ly/copynwin
It's all that matters.
Before a company / organization benefit from cloud computing, there are
several aspects relating to Security and Privacy below that must be
considered:
1. Risk Management and Compliance - organizations are starting to adopt
the cloud still be responsible for aspects of security management, risk,
and compliance with the rules applicable in the related industry. Risk
and compliance management requires a strong internal team and the
transparency of the process of cloud service providers.
Recommendation: cloud service providers have to use some or best
practice frameworks such as MOF, or ITIL, and have certifications such
as ISO / IEC 27001:2005, and publish the audit report to the SAS 70 Type
II. In addition, according to provisions of a state, may also have to
adhere to the PCI or FISMA.
2. Access and Identity Management - Identity can be obtained through
some cloud service providers, and must be interoperable between
different organizations, different cloud providers, and based on strong
process.
Recommendation: Authentication is recommended to use several factors at
once, such as biometrics, one time password tokens (such as token BCA),
ID card with a chip, and a password.
3. Integrity of Service - cloud-based services must be built with a
foundation of strong security, and operational processes must also be
integrated with security management in the organization. The cloud
service provider must follow the process that can be proven,
well-defined, and clearly in integrating security and privacy in
services ranging from the earliest point, at any point in the cycle,
until the final. Besides security management and auditing must be
aligned between cloud providers and customers.
Recommendation: Use such certification EAL4 + (for security evaluation),
SDL (for application development), ISO / IEC 18 044 (for incident
response)
4. Integrity Client - cloud services that are used on the client side
should pay attention to aspects of security, compliance, and integrity
on the client side. Integrity client can be improved by using a
combination of best practices.
Recommendation: Strengthen the desktop system, make sure the health of
desktop systems, apply the appropriate IT policy, identity federation,
Network Access Protection and so on.
5. Information Protection - Services cloud requires a reliable process
to protect the information before, during, and after the transaction.
Take advantage of data classification to improve the control of the data
is ready to be released into the clouds.
Recommendation: Use encryption technology and information rights
management (IRM) prior to data released to the cloud.
Tips
If an interested company to implement cloud services, here are some
tips:
Start with small things first, such as utilizing cloud services as
below: Email, Calendars, Contact, Messenger, Storage, Document /
Productivity, Photo, Group, News / Sport / Wheather, Synchronization
Devices (live mesh), Family Safety, Mobile, Map
Map business requirements to a cloud service, do not do the opposite.
Not necessarily cheaper cloud services, calculate the overall cost if
the system is used in full. Compare with the local system (on premise),
and also studied the possibility of combining the cloud service with
local system
Make the process of socialization and learning about cloud services to
all employees in the company
Study the possibility of technical issues such as interoperability,
architecture, and integration. Make sure that the format of files
created through the cloud services are also exactly the same as a local
application on the client sideCopy and WIN : http://bit.ly/copynwin
Copy and WIN : http://bit.ly/copynwin
Comments
Post a Comment